
Syed Solutions
Architecting Multi-Tier Solutions
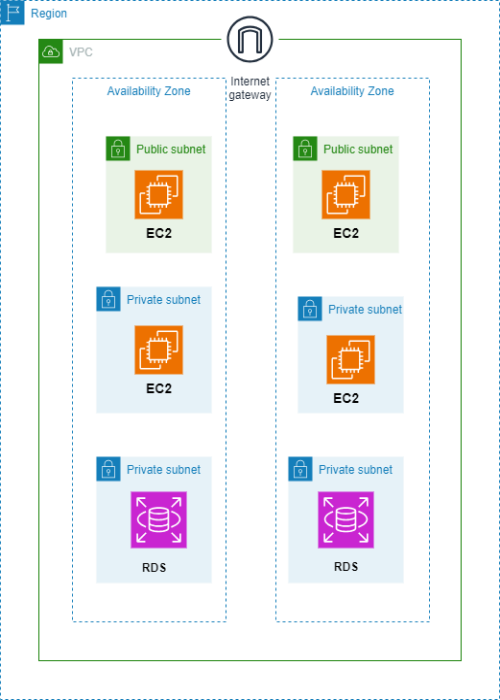
Designing a multi-tier architecture involves creating a structured and scalable system for your application, typically comprising three main tiers: presentation, application, and data.
The steps we take in designing your multi-tier solution are:
- We understand your application's requirements, including scalability, availability, performance, security, and compliance.
- We determine specific AWS services and features that align with your goals.
- Presentation Tier:The user interface and client-facing components.
- Application Tier:The logic and processing layer.
- Data Tier:The storage and database layer.
- We choose AWS services that best fit each tier's requirements. Common services include Amazon EC2, Lambda, Elastic Load Balancing, Amazon RDS, DynamoDB, and S3.
- We plan your network architecture using Amazon Virtual Private Cloud (VPC).
- We design subnets, security groups, and network ACLs to control traffic flow.
- We implement a Content Delivery Network (CDN) for improved content delivery.
- We deploy frontend components on Amazon EC2 instances or serverless platforms like AWS Amplify.
- We use Amazon CloudFront for content delivery and caching.
- We implement security measures such as AWS Web Application Firewall (WAF) and SSL certificates.
- We host application logic on Amazon EC2 instances, AWS Fargate, or AWS Lambda functions.
- We implement auto-scaling based on traffic patterns using Amazon EC2 Auto Scaling or Lambda triggers.
- We use AWS Elastic Load Balancing to distribute traffic.
7. Data Tier:
- We choose the appropriate database service: Amazon RDS for relational databases, Amazon DynamoDB for NoSQL, or other specialized databases.
- We implement data replication and backup strategies.
- We use Amazon S3 for object storage, data lakes, or backups.
- We implement IAM policies for fine-grained access control.
- We encrypt data at rest and in transit using AWS Key Management Service (KMS) and SSL/TLS.
- We follow AWS Well-Architected Framework and best practices for security and compliance.
- We set up monitoring using AWS CloudWatch for metrics and alarms.
- We configure AWS CloudTrail for auditing and AWS Config for resource tracking.
- We implement centralized logging with Amazon CloudWatch Logs or services like Amazon Elasticsearch.
- We deploy resources across multiple Availability Zones (AZs) or regions for redundancy.
- We use Amazon Route 53 for DNS failover and load balancing.
- We create automated backup and recovery procedures.
- We continuously monitor and optimize your architecture for cost-effectiveness and performance.
- We use AWS Trusted Advisor and other AWS tools to identify cost-saving opportunities.
- We conduct thorough testing, including load testing, to ensure your architecture can handle expected traffic loads.
- We document your architecture, including diagrams, configurations, and procedures for maintenance and troubleshooting.
- We use Infrastructure as Code (IaC) tools like AWS CloudFormation or AWS CDK to automate the deployment and management of your architecture.